Step 1: Install System
Packages
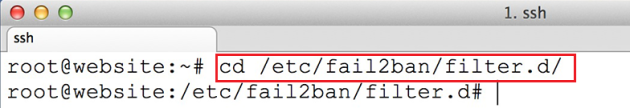
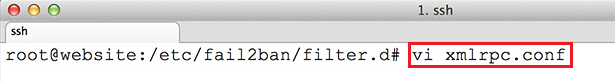
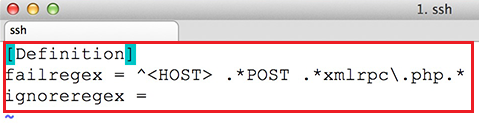
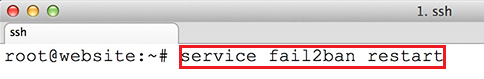
1. Before we proceed with Zimbra
Collaboration Suite installation process, first login to your server console
with root privileges and install the following packages:
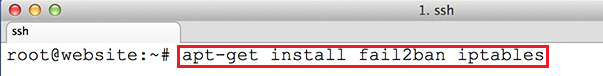
# yum -y install unzip
net-tools sysstat openssh-clients perl-core libaio nmap-ncat libstdc++.so.6
2. Next, issue getenforce command to check if Selinux in enabled
on your machine. In case the policy is set to Enforced disable it by issuing the below
commands:
# getenforce
# setenforce 0
# getenforce
To completely disable Selinux on CentOS, open /etc/selinux/config file with a text editor and set the line
SELINUX to disabled.
3. Assure that wget system utility is
also installed on your system by issuing the following command:
Step 2: Configure System
Hostname
4. In order for Zimbra to function correctly you must set the
local machine hostname and FQDN to point to your server IP Address by running
the below commands from root account:
# hostnamectl set-hostname mail
# echo "192.168.0.14 mail.mentor-global.net mail " >> /etc/hosts
# cat /etc/hosts
Replace the system hostname and FQDN values accordingly in order
to match your own domain settings. Test the hostname and FQDN values by issuing
the ping command against
both records.
# ping -c1 mail.mentor-global.net
# ping -c1 mail
Step 3: Add a Static IP
Address
5. If your server uses a DHCP dynamic IP
Address, then you need to edit your network interface card and configure to use
a static IP Address. Get the network interfaces information using ip addr command and identify your server
external NIC (usually something like enp0s3 or eth0).
Then, run the nmtui-edit command against the interface you need to change settings
and assign the interface with a manual IP Address. Use the below screenshots as
a guide.
Step 4: Disable Unwanted
Services
6. A CentOS 7 default installation ships
with postfix daemon already
installed and running. To disable and erase postfix service run the following
commands:
# systemctl stop postfix
# systemctl disable postfix
# yum remove postfix
After the service has been removed issue the ss command in order to check if other
daemons incompatible with Zimbra service, such as LDAP, httpd, dovecot are
running on your system. If that’s the case remove them as well.
Step 5: Install Zimbra
Collaboration Suite Open Source Edition
----------------- For RHEL/CentOS 7 -----------------
# wget
https://files.zimbra.com/downloads/8.6.0_GA/zcs-8.6.0_GA_1153.RHEL7_64.20141215151110.tgz
----------------- For RHEL/CentOS 6 -----------------
# wget
https://files.zimbra.com/downloads/8.6.0_GA/zcs-8.6.0_GA_1153.RHEL6_64.20141215151155.tgz
8. After the download completes, use unzip command to extract the archive, enter zimbra
extracted directory and list the directory content to locate the installer
file.
# tar xfz zcs-8.6.0_GA_1153.RHEL7_64.20141215151110.tgz
# cd zcs-8.6.0_GA_1153.RHEL7_64.20141215151110
# ls
9. Now, start Zimbra installation
process by launching in execution the installer script file named install.sh.
After a series of system checks the installer will prompt you to
accept the license. Agree the license (y) in order to continue further with the
installation process.
# ./install.sh
OR
# ./install.sh --platform-override [On different platforms other than RHEL]
Sample Output
Operations logged to /tmp/install.log.12951
Checking for existing installation...
zimbra-ldap...NOT FOUND
zimbra-logger...NOT FOUND
zimbra-mta...NOT FOUND
zimbra-dnscache...NOT FOUND
zimbra-snmp...NOT FOUND
zimbra-store...NOT FOUND
zimbra-apache...NOT FOUND
zimbra-spell...NOT FOUND
zimbra-convertd...NOT FOUND
zimbra-memcached...NOT FOUND
zimbra-proxy...NOT FOUND
zimbra-archiving...NOT FOUND
zimbra-core...NOT FOUND
PLEASE READ THIS AGREEMENT CAREFULLY BEFORE USING THE SOFTWARE.
ZIMBRA, INC. ("ZIMBRA") WILL ONLY LICENSE THIS SOFTWARE TO YOU IF YOU
FIRST ACCEPT THE TERMS OF THIS AGREEMENT. BY DOWNLOADING OR INSTALLING
THE SOFTWARE, OR USING THE PRODUCT, YOU ARE CONSENTING TO BE BOUND BY
THIS AGREEMENT. IF YOU DO NOT AGREE TO ALL OF THE TERMS OF THIS
AGREEMENT, THEN DO NOT DOWNLOAD, INSTALL OR USE THE PRODUCT.
License Terms for the Zimbra Collaboration Suite:
http://www.zimbra.com/license/zimbra-public-eula-2-5.html
Do you agree with the terms of the software license agreement? [N] y
10. Next, the installation process will prompt
you a series of questions in order to configure zimbra daemon properly. Use the
below installation excerpt in order to setup zimbra service further.
Checking for prerequisites...
FOUND: NPTL
FOUND: sudo-1.8.6p7-13
FOUND: libidn-1.28-3
FOUND: gmp-6.0.0-11
FOUND: /usr/lib/libstdc++.so.6
Checking for suggested prerequisites...
FOUND: sysstat
FOUND: sqlite
Prerequisite check complete.
Checking for installable packages
Found zimbra-core
Found zimbra-ldap
Found zimbra-logger
Found zimbra-mta
Found zimbra-dnscache
Found zimbra-snmp
Found zimbra-store
Found zimbra-apache
Found zimbra-spell
Found zimbra-memcached
Found zimbra-proxy
Select the packages to install
Install zimbra-ldap [Y] y
11. Next, it will ask you to install the zimbra
packages, press Y to install all.
Select the packages to install
Install zimbra-ldap [Y] y
Install zimbra-logger [Y] y
Install zimbra-mta [Y] y
Install zimbra-dnscache [Y] y
Install zimbra-snmp [Y] y
Install zimbra-store [Y] y
Install zimbra-apache [Y] y
Install zimbra-spell [Y] y
Install zimbra-memcached [Y] y
Install zimbra-proxy [Y] y
Checking required space for zimbra-core
Checking space for zimbra-store
Checking required packages for zimbra-store
zimbra-store package check complete.
Installing:
zimbra-core
zimbra-ldap
zimbra-logger
zimbra-mta
zimbra-dnscache
zimbra-snmp
zimbra-store
zimbra-apache
zimbra-spell
zimbra-memcached
zimbra-proxy
You appear to be installing packages on a platform different
than the platform for which they were built.
This platform is UNKNOWN_64
Packages found: RHEL7_64
This may or may not work.
Using packages for a platform in which they were not designed for
may result in an installation that is NOT usable. Your support
options may be limited if you choose to continue.
Install anyway? [N] y
12. Finally, it will start zimbra installation
process.
The system will be modified. Continue? [N] y
Removing /opt/zimbra
Removing zimbra crontab entry...done.
Cleaning up zimbra init scripts...done.
Cleaning up /etc/ld.so.conf...done.
Cleaning up /etc/security/limits.conf...done.
Finished removing Zimbra Collaboration Server.
Installing packages
zimbra-core......zimbra-core-8.6.0_GA_1153.RHEL7_64-20141215151110.x86_64.rpm...
zimbra-ldap......zimbra-ldap-8.6.0_GA_1153.RHEL7_64-20141215151110.x86_64.rpm...done
zimbra-logger......zimbra-logger-8.6.0_GA_1153.RHEL7_64-20141215151110.x86_64.rpm...done
zimbra-mta......zimbra-mta-8.6.0_GA_1153.RHEL7_64-20141215151110.x86_64.rpm...done
zimbra-dnscache......zimbra-dnscache-8.6.0_GA_1153.RHEL7_64-20141215151110.x86_64.rpm...done
zimbra-snmp......zimbra-snmp-8.6.0_GA_1153.RHEL7_64-20141215151110.x86_64.rpm...done
zimbra-store......zimbra-store-8.6.0_GA_1153.RHEL7_64-20141215151110.x86_64.rpm...done
zimbra-apache......zimbra-apache-8.6.0_GA_1153.RHEL7_64-20141215151110.x86_64.rpm...done
zimbra-spell......zimbra-spell-8.6.0_GA_1153.RHEL7_64-20141215151110.x86_64.rpm...done
zimbra-memcached......zimbra-memcached-8.6.0_GA_1153.RHEL7_64-20141215151110.x86_64.rpm...done
zimbra-proxy......zimbra-proxy-8.6.0_GA_1153.RHEL7_64-20141215151110.x86_64.rpm...done
Operations logged to /tmp/zmsetup01262016-002704.log
Installing LDAP configuration database...done.
Setting defaults...No results returned for A lookup of mail.mentor-global.net
Checked nameservers:
12.168.0.1
8.8.8.8
No results returned for AAAA lookup of mail.mentor-global.net Checked nameservers:
12.168.0.1
8.8.8.8
DNS ERROR resolving mail.mentor-global.net
It is suggested that the hostname be resolvable via DNS
Change hostname [Yes] yes
Please enter the logical hostname for this host [mail.mentor-global.net]
No results returned for A lookup of mail.mentor-global.net
Checked nameservers:
12.168.0.1
8.8.8.8
DNS ERROR resolving mail.mentor-global.net
It is suggested that the hostname be resolvable via DNS
Re-Enter hostname [Yes] no
DNS ERROR resolving MX for mail.mentor-global.net
It is suggested that the domain name have an MX record configured in DNS
Change domain name? [Yes] no
done.
Checking for port conflicts
Main menu
1) Common Configuration:
2) zimbra-ldap: Enabled
3) zimbra-logger: Enabled
4) zimbra-mta: Enabled
5) zimbra-dnscache: Enabled
6) zimbra-snmp: Enabled
7) zimbra-store: Enabled
+Create Admin User: yes
+Admin user to create: admin@mail.mentor-global.net
******* +Admin Password UNSET
+Anti-virus quarantine user: virus-quarantine.7xi47__k@mail.mentor-global.net +Enable automated spam training: yes
+Spam training user: spam.wasleuiv@mail.mentor-global.net
+Non-spam(Ham) training user: ham.wzmkmrkq@mail.mentor-global.net
+SMTP host: mail.mentor-global.net
+Web server HTTP port: 8080
+Web server HTTPS port: 8443
+Web server mode: https
+IMAP server port: 7143
+IMAP server SSL port: 7993
+POP server port: 7110
+POP server SSL port: 7995
+Use spell check server: yes
+Spell server URL: http://mail. mentor-lobal.net:7780/aspell.php
+Enable version update checks: TRUE
+Enable version update notifications: TRUE
+Version update notification email: admin@mail.mentor-global.net
+Version update source email: admin@mail.mentor-global.net
+Install mailstore (service webapp): yes
+Install UI (zimbra,zimbraAdmin webapps): yes
8) zimbra-spell: Enabled
9) zimbra-proxy: Enabled
10) Default Class of Service Configuration:
s) Save config to file
x) Expand menu
q) Quit
Address unconfigured (**) items (? - help) 7
13. Store configuration.
1) Status: Enabled
2) Create Admin User: yes
3) Admin user to create: admin@mail.mentor-global.net
** 4) Admin Password UNSET
5) Anti-virus quarantine user: virusquarantine.7xi47__k@mail.mentor-global.net
6) Enable automated spam training: yes
7) Spam training user: spam.wasleuiv@mail.mentor-global.net
8) Non-spam(Ham) training user: ham.wzmkmrkq@mail.mentor-global.net 9) SMTP host: mail.mentor-global.net
10) Web server HTTP port: 8080
11) Web server HTTPS port: 8443
12) Web server mode: https
13) IMAP server port: 7143
14) IMAP server SSL port: 7993
15) POP server port: 7110
16) POP server SSL port: 7995
17) Use spell check server: yes
18) Spell server URL: http://mail.mentor-global.net:7780/aspell.php
19) Enable version update checks: TRUE
20) Enable version update notifications: TRUE
21) Version update notification email: admin@mentor-global.net
22) Version update source email: admin@mentor-global.net
23) Install mailstore (service webapp): yes
24) Install UI (zimbra,zimbraAdmin webapps): yes
Select, or 'r' for previous menu [r] 4 # Select 4 to set admin password
Password for admin@mail.mentor-global.net (min 6 characters): [54mE0RmqN] enter admin password here
Store configuration
1) Status: Enabled
2) Create Admin User: yes
3) Admin user to create: admin@mentor-global.net
4) Admin Password set
5) Anti-virus quarantine user: virus-quarantine.7xi47__k@mail. mentor-global.net
6) Enable automated spam training: yes
7) Spam training user: spam.wasleuiv@mentor-global.net
8) Non-spam(Ham) training user: ham.wzmkmrkq@mentor-global.net
9) SMTP host: mail.mentor-global.net
10) Web server HTTP port: 8080
11) Web server HTTPS port: 8443
12) Web server mode: https
13) IMAP server port: 7143
14) IMAP server SSL port: 7993
15) POP server port: 7110
16) POP server SSL port: 7995
17) Use spell check server: yes
18) Spell server URL: http://mail.mentor-global.net:7780/aspell.php
19) Enable version update checks: TRUE
20) Enable version update notifications: TRUE
21) Version update notification email: admin@mentor-global.net
22) Version update source email: admin@mentor-global.net
23) Install mailstore (service webapp): yes
24) Install UI (zimbra,zimbraAdmin webapps): yes
Select, or 'r' for previous menu [r] r
Main menu
1) Common Configuration:
2) zimbra-ldap: Enabled
3) zimbra-logger: Enabled
4) zimbra-mta: Enabled
5) zimbra-dnscache: Enabled
6) zimbra-snmp: Enabled
7) zimbra-store: Enabled
8) zimbra-spell: Enabled
9) zimbra-proxy: Enabled
10) Default Class of Service Configuration:
s) Save config to file
x) Expand menu
q) Quit
*** CONFIGURATION COMPLETE - press 'a' to apply
Select from menu, or press 'a' to apply config (? - help) a # Apply configuration
Save configuration data to a file? [Yes] Enter
Save config in file: [/opt/zimbra/config.11047]
Saving config in /opt/zimbra/config.11047...done.
The system will be modified - continue? [No] yes
Operations logged to /tmp/zmsetup01262016-002704.log
Setting local config values...done.
Initializing core config...Setting up CA...done.
Deploying CA to /opt/zimbra/conf/ca ...done.
Creating SSL zimbra-store certificate...done.
Creating new zimbra-ldap SSL certificate...done.
Creating new zimbra-mta SSL certificate...done.
Creating new zimbra-proxy SSL certificate...done.
Installing mailboxd SSL certificates...done.
Installing MTA SSL certificates...done.
Installing LDAP SSL certificate...done.
Installing Proxy SSL certificate...done.
Initializing ldap...done.
Setting replication password...done.
Setting Postfix password...done.
Setting amavis password...done.
Setting nginx password...done.
Setting BES searcher password...done.
Creating server entry for mail.mentor-global.net...done.
Setting Zimbra IP Mode...done.
Saving CA in ldap ...done.
Saving SSL Certificate in ldap ...done.
Setting spell check URL...done.
Setting service ports on mail.mentor-global.net...done.
Setting zimbraFeatureTasksEnabled=TRUE...done.
Setting zimbraFeatureBriefcasesEnabled=TRUE...done.
Setting Master DNS IP address(es)...done.
Setting DNS cache tcp lookup preference...done.
Setting DNS cache udp lookup preference...done.
Setting DNS tcp upstream preference...done.
Setting TimeZone Preference...done.
Initializing mta config...done.
Setting services on mail.mentor-global.net...done.
Adding mail.mentor-global.net to zimbraMailHostPool in default COS...done.
Creating domain mail.mentor-global.net...done.
Setting default domain name...done.
Creating domain mail.mentor-global.net already exists.
Creating admin account admin@mail.mentor-global.net...done.
Creating root alias...done.
Creating postmaster alias...done.
Creating user spam.wasleuiv@mentor-global.net...done.
Creating user ham.wzmkmrkq@mentor-global.net...done.
Creating user virus-quarantine.7xi47__k@ mentor-global.net...done.
Setting spam training and Anti-virus quarantine accounts...done.
Initializing store sql database...done.
Setting zimbraSmtpHostname for mail.mentor-global.net...done.
Configuring SNMP...done.
Setting up syslog.conf...done.
Starting servers...done.
Installing common zimlets...
com_zimbra_adminversioncheck...done.
com_zimbra_attachcontacts...done.
com_zimbra_attachmail...done.
com_zimbra_bulkprovision...done.
com_zimbra_cert_manager...done.
com_zimbra_clientuploader...done.
com_zimbra_date...done.
com_zimbra_email...done.
com_zimbra_mailarchive...done.
com_zimbra_phone...done.
com_zimbra_proxy_config...done.
com_zimbra_srchhighlighter...done.
com_zimbra_tooltip...done.
com_zimbra_url...done.
com_zimbra_viewmail...done.
com_zimbra_webex...done.
com_zimbra_ymemoticons...done.
Finished installing common zimlets.
Restarting mailboxd...done.
Creating galsync account for default domain...done.
You have the option of notifying Zimbra of your installation.
This helps us to track the uptake of the Zimbra Collaboration Server.
The only information that will be transmitted is:
The VERSION of zcs installed (8.6.0_GA_1153_RHEL7_64)
The ADMIN EMAIL ADDRESS created (admin@mentor-global.net)
Notify Zimbra of your installation? [Yes] no
Notification skipped
Setting up zimbra crontab...done.
Moving /tmp/zmsetup01262016-002704.log to /opt/zimbra/log
Configuration complete - press return to exit # Press Enter
Step 6: Zimba Initial
Configuration
14. After the installation finishes, open a web
browser and navigate to your domain name or IP address of the machine running
zimbra service, on port 7071 via HTTPS
protocol, accept the certificate security error and login with the credentials
configured during the installation process. The default username for Zimbra
Admin web panel is admin.
https://mail.mentor-global.net:7071
or
https://192.168.1.14:7071
Zimbra Login
15. Once logged in the admin web console you can
start adding your own SSL certificates,
create mail accounts, mail aliases and so on. Just remember that the port 7071 is used only for administrative tasks.
Clients
can securely login to their webmail boxes using the domain name or the server
IP address via HTTPS protocol.
https://mail.mentor-global.net
or
https://192.168.1.14
User Webmail Login
User Webmail Dashboard
Congratulations!
Now you have a full operating mail stack installed on your premises.
Step 6: Remove or
Uninstall Zimbra
If you wish to uninstall Zimbra service alongside with its
components run the installer script with the -u option.
To delete
Zimbra installation archive and directory run the below commands: